by frank | Nov 16, 2020 | AV, Blue Team, Security
Reading Time: 4 minutesMSF (Metasploit) version 6. Network possible detection ? OJ ( @TheColonial ) is a clever guy and a main contributor to the open source project of Metasploit. One of MSF6’s goal is to get rid of Strings in order to fly even lower … so close to...
by frank | Oct 26, 2020 | AV, Security, Windows
Reading Time: 3 minutesThe other day, I was shadowing a colleague of me who was doing a red team. The client was running McAfee AV. While the reputation of that AV isn’t the best, it got a bit in the way for a few minutes. After doing a lateral movement, my...
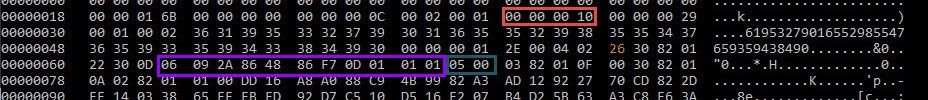
by frank | Mar 26, 2020 | Blue Team, Palo Alto, Security, Windows
Reading Time: 4 minutesBefore reading note: for practical reasons (time consuming) not all the printscreen shots have been made with same settings (ip addresses mainly i used once 192.168.150.196 and sometimes 192.168.1.71) For tests i created a simple reverse_http...
by frank | Jul 31, 2023 | AV, Palo Alto, Red team, Security
Reading Time: < 1 minutecyvrfsfd.sys : Palo Alto Networks cyvrlpc.sys : Palo Alto Networks tedrdrv.sys : Palo Alto Networks cyvrmtgn.sys : Palo Alto Networks cyverak.sys : cyvera, Palo Alto Networks tedrpers-7.???.sys : Palo Alto Networks cyinjct.dll : Palo Alto...
by frank | Jul 7, 2023 | Blue Team, Red team, Security, Windows
Reading Time: 2 minutesLast few days, I’ve been playing with the WFP componant of Windows. WFP = Windows Filtering platform Many informations blogs are existing like the great one from Pavel who really deeped dive into it which I recommand to read Introduction...
by frank | Jun 1, 2023 | Security
Reading Time: 3 minutesThis is under construction Commands to troubleshoot your WEC/WEF Forwardings PS Code to get status of the Listener winrm e winrm/config/listener PS Code to get status of a Forwarding Channel wecutil gr Security Above we see only one Active...
by frank | Jun 1, 2023 | Security
Reading Time: < 1 minuteStep 2.1 : Kibana Download latest release of Kibana here : https://www.elastic.co/cn/downloads/kibana It’s a large zip file. Extract the zip file to C:\Program Files Run a CMD as Admin cd “C:\Program...
by frank | Apr 3, 2023 | Security
Reading Time: < 1 minuteThe following 10 quick wins, will not prevent you to be full 100% hack proof, but I promiss you, if you are able to implement those 10 things, then a hacker will have much more trouble to become a Domain Admin user from a simple User, to...
by frank | Apr 3, 2023 | Security
Reading Time: 2 minutesSummary While there isn’t anything necessarily inherently insecure about AD CS (except for ESC8 as detailed below), it is surprisingly easy to misconfigure its various elements, resulting in ways for unelevated users to escalate in the...
by frank | Nov 22, 2022 | Security
Reading Time: 5 minutesThis article is more of a my own notes and it may profit to others. This is a DRAFT for the moment. Recently, I followed a course on developement on Offensive Driver Developpement from zeropointsecurity (link here). I recommend following it,...
by frank | Oct 24, 2022 | Palo Alto, Red team, Security
Reading Time: 2 minutesSince Mr. D0x post on XDR : https://twitter.com/mrd0x/status/1514318257112637440 things have improved. https://mrd0x.com/cortex-xdr-analysis-and-bypass/ Palo Alto has introduced an cipher to crypt the techsupport file. Password to be calculated...
by frank | Oct 3, 2022 | Security
Reading Time: < 1 minuteAs of date 3.10.2022...
by frank | Mar 11, 2022 | Blue Team, Red team, Security, Windows
Reading Time: 3 minutesGithub repo for the tool of Antonio Cocomazzi @splinter_code and Andrea Pierini @decoder_it : https://github.com/antonioCoco/RemotePotato0 Potato what ? In the last few years, we saw tools likes RottenPotato, RottenPotatoN, SweetPotato, Juicy...



Recent Comments