by frank | Jan 8, 2021 | Blue Team, C2C, Security
Reading Time: < 1 minuteFollowing the really interesting article of Tek : https://www.randhome.io/blog/2020/12/20/analyzing-cobalt-strike-for-fun-and-profit/ Where he described how to get a valid URL for CobaltStrike, I tried to check if it was the same for...
by frank | Jan 5, 2021 | AV, Blue Team, Red team, Security, Windows
Reading Time: < 1 minuteDriver : SentinelMonitor Altitude 389040 Services: Name=LogProcessorService; DisplayName=SentinelOne Agent Log Processing Service; ServiceName=LogProcessorServiceName=SecurityHealthService; DisplayName=Windows Security Service;...
by frank | Jan 4, 2021 | AV, Blue Team, Red team, Security, Windows
Reading Time: 2 minutesYou can download this CSV file here <==== SHA256NameSignerDescription—————————04A85E359525D662338CAE86C1E59B1D7AA9BD12B920E8067503723DC1E03162ADV64DRV.sys”FUJITSU LIMITED...
by frank | Nov 17, 2020 | Blue Team
Reading Time: 5 minutesgit clone https://github.com/volatilityfoundation/volatility3.git Then download symbol table packs for the operating systems you need to analyze: https://downloads.volatilityfoundation.org/volatility3/symbols/windows.zip...
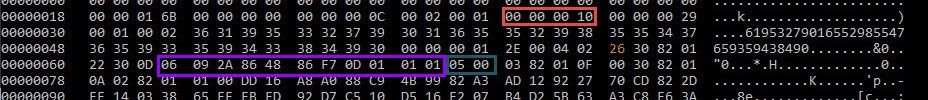
by frank | Nov 16, 2020 | AV, Blue Team, Security
Reading Time: 4 minutesMSF (Metasploit) version 6. Network possible detection ? OJ ( @TheColonial ) is a clever guy and a main contributor to the open source project of Metasploit. One of MSF6’s goal is to get rid of Strings in order to fly even lower … so close to...
by frank | Oct 13, 2020 | Blue Team, Red team, Security, Windows
Reading Time: < 1 minuteto check if a Win domain is a possible candidate to a MITM WSUS attack check reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer https://github.com/pimps/wsuxploit/ (requires a MITM attack for ex. with bettercap)...


Recent Comments