cyvrfsfd.sys : Palo Alto Networks
cyvrlpc.sys : Palo Alto Networks
tedrdrv.sys : Palo Alto Networks
cyvrmtgn.sys : Palo Alto Networks
cyverak.sys : cyvera, Palo Alto Networks
tedrpers-7.???.sys : Palo Alto Networks
cyinjct.dll : Palo Alto Networks
ntnativeapi.dll : Palo Alto Networks
cyvera.dll : Palo Alto Networks
cyvrtrap.dll : Palo Alto Networks
amsi.dll : defender
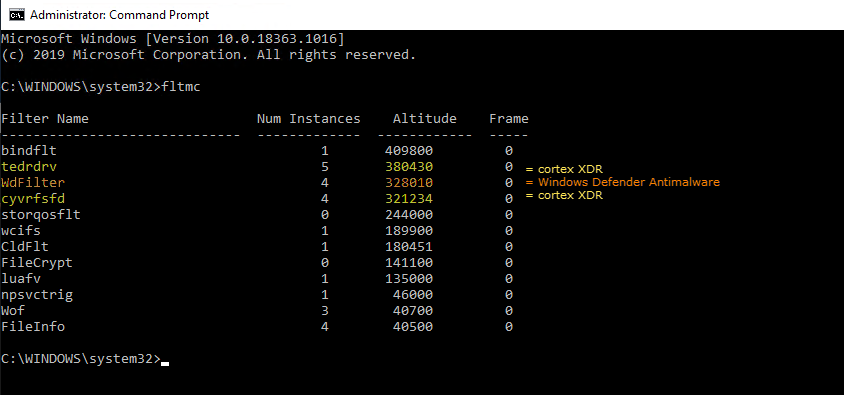
\\\\.\\CyvrMitAnd the altitude signature of the two drivers 380430 and 321234 (nice number 🙂
328010 is for Windows Defender.
DLL injected into processes is : cyinjct.dll (0fed3ea714f128a1db3be30bd7b4c905ff3e50592f1381dae235200311f88af6) for this version
There is also cyvera.dll and cyvrtrap.dll
Hooked functions
KernelBase
CreateFileA
LoadLibraryExW
LoadLibraryA
LoadLibraryExA
VirtualAlloc
VirtualProtect
HeapCreate
VirtualAllocEx
VirtualProtectEx
LoadLibraryW
NTDLL
NtSetInformationThread
NtOpenThreadToken
NtOpenProcess
NtSetInformationFile
NtMapViewOfSection
NtUnmapViewOfSection
NtOpenThreadTokenEx
NtOpenProcessTokenEx
NtOpenFile
NtQueryAttributesFile
Full hooked functions have been gathered here by Mr-Un1k0d3r https://raw.githubusercontent.com/Mr-Un1k0d3r/EDRs/main/cortex.txt
Configuration files
ldb files (see https://mrd0x.com/cortex-xdr-analysis-and-bypass/ )
BruteForce cytool password : https://twitter.com/k4nfr3/status/1514655268554133508
YaraSignatures_xxx.yara
dse_rules_8_xxx_windows_encrypt.clp
Cortex XDR uses CLIPS language for their rules : https://www.clipsrules.net/
interesting strings in some dll files with highest entropy can sometimes lead to information disclosure, which has been fixed by PAN by ethical disclosure but no public annoucement.
2r5u8xQeTjWnZr4u7x!A%C*F-hWmZq4t
A
BF27D8Gx#ns@R~J~8SX2205DBAPq40
and
3bGJoIHBuYSBlcm5wdSB6ciBiYSB4NGFzZTNAY2ViZ2Jhem52eS5wYno=
{4544A023-2767-411C-86E4-3EA52A4AA172} {849BDEF4-C2D5-4464-96E8-3CBE11841AD6}
6

Recent Comments