Following the really interesting article of Tek : https://www.randhome.io/blog/2020/12/20/analyzing-cobalt-strike-for-fun-and-profit/
Where he described how to get a valid URL for CobaltStrike, I tried to check if it was the same for Metasploit as he mentionned.
Didier Stevens also has this in his tools : https://blog.didierstevens.com/2020/01/27/update-hash-py-version-0-0-8/
hash.py -a checksum8 #aaa9 => 15c => 5C == 92 which is a valid MetaSploit Checksum.
But testing it myself, showed it didn’t work on my Metasploit C2C server.
Looking again at the Metasploit source code : https://github.com/rapid7/metasploit-framework/blob/master/lib/rex/payloads/meterpreter/uri_checksum.rb
a few other checks popup and there is a minimum length calculation.
So I changed the minimum length from Tek’s code to 27
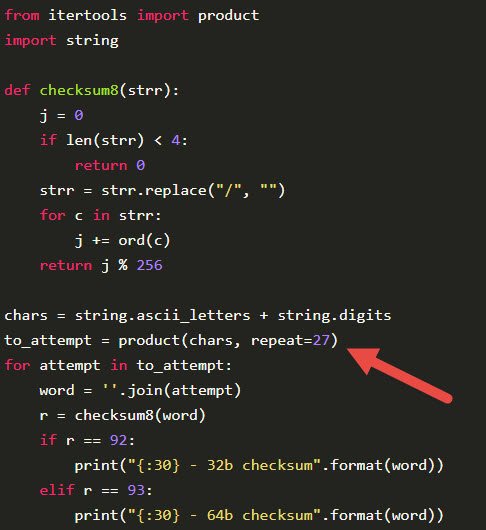
Output of the tool is :
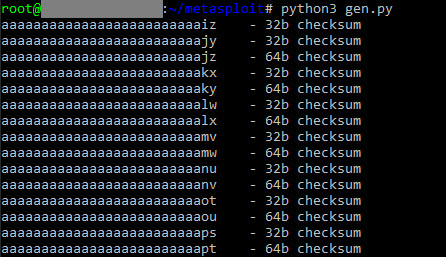
wget --no-check-certificate -O metasploit.bin --user-agent="Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko" https://192.168.1.5/aaaaaaaaaaaaaaaaaaaaaaaaaiz
curl --insecure -O metasploit.bin –A "Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like Gecko" https://192.168.1.5/aaaaaaaaaaaaaaaaaaaaaaaaaiz
Bingo, the meterpreter is being downloaded.
1
Recent Comments