Part 1 out of 3
WEC = WEF = Windows event collection are different words but are all refering to the same functionality.
If there is one thing I’ve learned over the last year. Hardly nobody has a full proof cybersecurity system. And I read Forensic reports and what comes again and again is ….
Translated to simple words. No logs, no proofs, no idea what happens and worst, no Idea how the hackers came in and what data was exfiltrated.
GDPR and the mental burden to not know how this has happen is quite hard to endure.
So here is a fairly simple project.
Build a capability running on a old hardware you probably don’t use any more, with one or two large disks, just to capture everything what is happening.
So either when a breach occurs or a simple questioning if something is happening ( example you want to enforce RunAsPPL on Lsass but can’t take much risk, you want to enable Audit Mode on lsass.exe (see article from microsoft here). And if after a period of time not a single of those Event 3065 or 3066 then you are safe to push your GPO to your entire domain including servers.
Here is a excellent reference guide : WEC Cookbook by Elastic Search = https://ela.st/tjs-wec-cookbook
Requirement:
Hardware server running Windows (can be server or worstation) which is joined to your domain. It should have at least 8 Gb of Ram and depending of the amount of machines in your Domain, a few Terras of hard-disk will keep all your logs for at least 30 days.
Make sure, that Domain Users, Servers Admins and oven DA cannot logon to your machine, only local accounts can login (just in case of a DA account is been compromised ). You can even disable RDP to be safer.
Or if you feel more into it, then install the ElasticSearch and Kibana on a Linux machine of your choice (not descrived in this article).
Count roughly a few hours to complete this entire procedure.
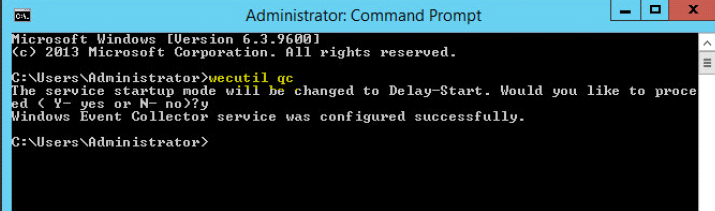
Step 1 : Enable Windows Event Collector service (wecsvc)
On the collector : in a command prompt as Administrator type
wecutil qc
Step 2: Set up Event Subscriptions (push method)
mmc
Add Event Viewer
Subscriptions / Create Subscription
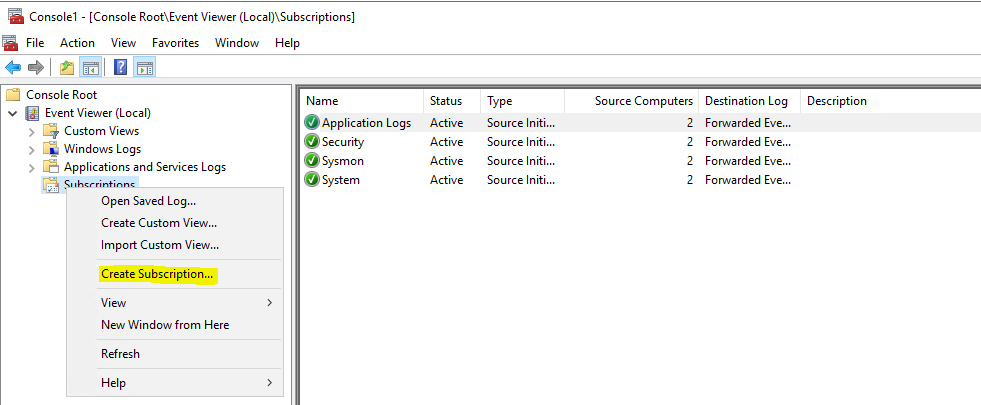
Enter Subscription name
Select Source computer initiated ( = push from computers to Collector)
Click on Select Computer Groups
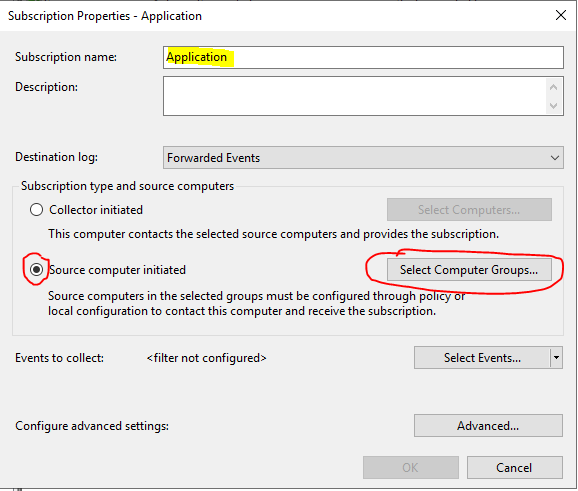
Click on Add Domain Computers
Enter the group name of all the machines you want to monitor. I’ve created a group called ALL_WS
Click twice on OK
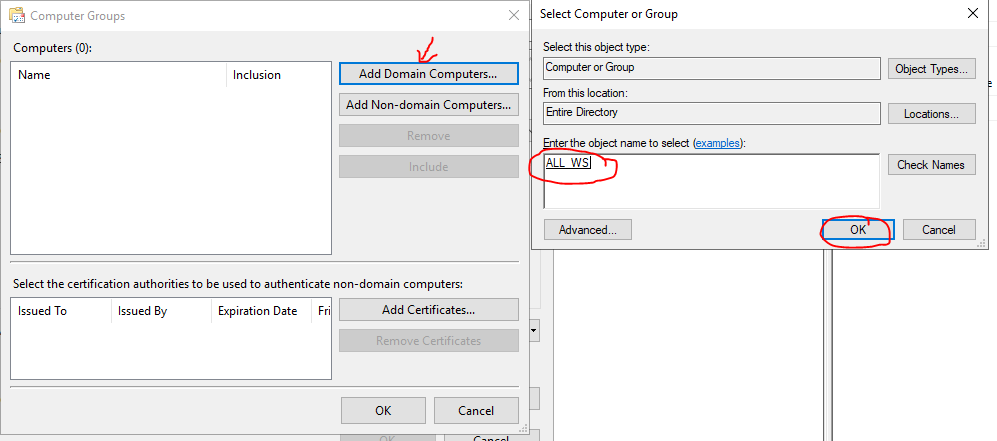
Click on Select Events
And Select which events . Here we are doing Application
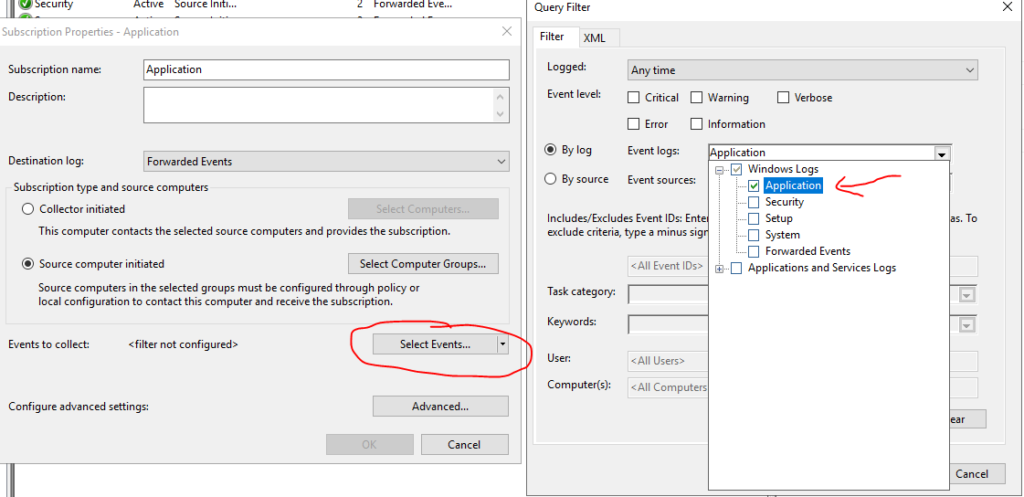
Click on Advanced
Select Minimize Latency
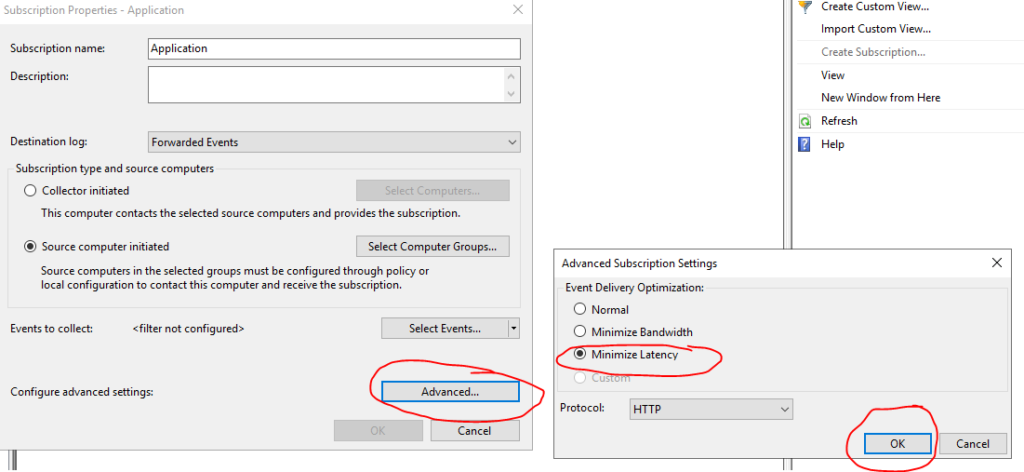
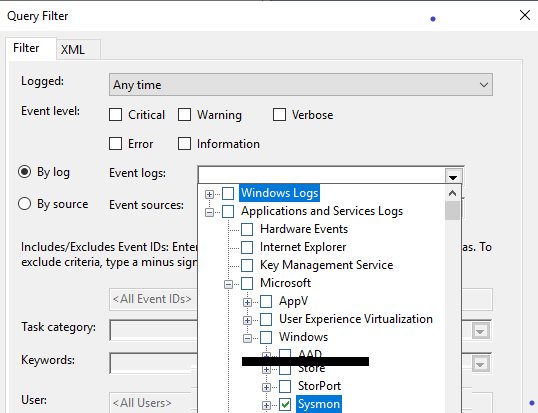
After doing this for the 3 standards ones
The 4th is SYSMON You can find it under
Applications and Services Logs / Microsoft / Windows / Sysmon
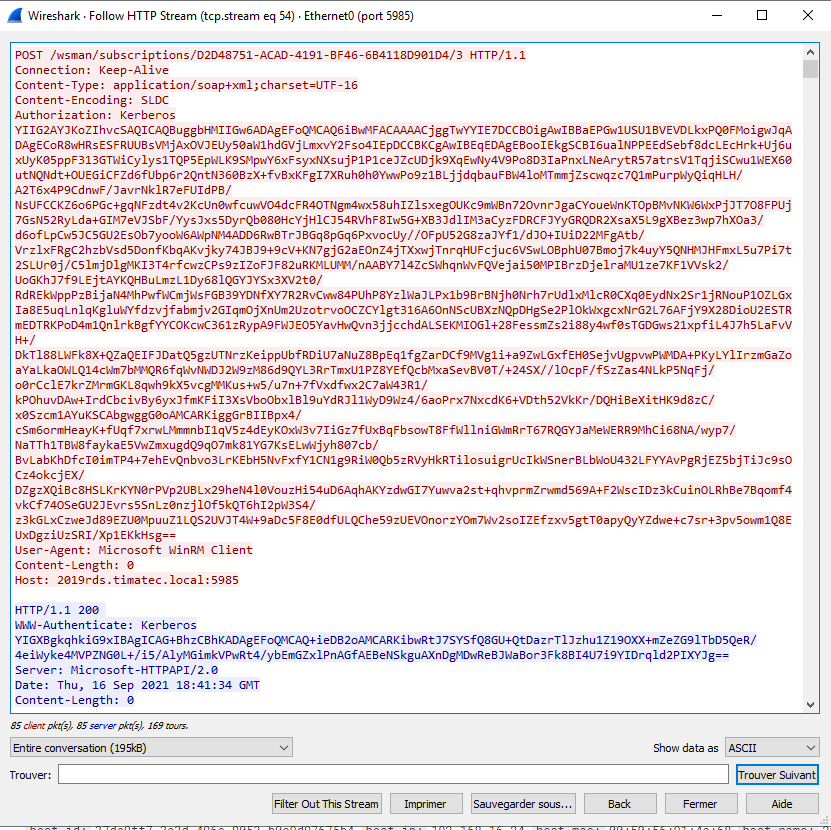
Little Note here : You might think that event forwarding is not safe by HTTP. Indeed HTTP is not encrypted but the content is
See the pcap of the HTTP flow from a computer to the Collector
Step 3: fix ACL on Collector
There is a bug sometimes on server OS to run WECSVC. I won't go into details, read the article if you want, but run the below (it won't harm
under a CMD running with admin privilege :
check existing ACL with :
netsh http show urlacl
If you see the below, then nothing to do, other ways, recreate the correct ACL with the following 4 lines. (This will save you some time debugging why you get 404 errors when client push their events to the Collector)
netsh http delete urlacl url=http://+:5985/wsman/
netsh http add urlacl url=http://+:5985/wsman/ sddl=D:(A;;GX;;;S-1-5-80-569256582-2953403351-2909559716-1301513147-412116970)(A;;GX;;;S-1-5-80-4059739203-877974739-1245631912-527174227-2996563517)
netsh http delete urlacl url=https://+:5986/wsman/
netsh http add urlacl url=https://+:5986/wsman/ sddl=D:(A;;GX;;;S-1-5-80-569256582-2953403351-2909559716-1301513147-412116970)(A;;GX;;;S-1-5-80-4059739203-877974739-1245631912-527174227-2996563517)
And restart the services :
sc stop winrm
sc stop wecsvc
sc start winrm
sc start wecsvc
Reference : https://docs.microsoft.com/en-US/troubleshoot/windows-server/admin-development/events-not-forwarded-by-windows-server-collector
Recent Comments